Auth Server Configuration
Jans Lock Token Stream Service#
To enable Jans Auth PubSub messages 2 configuration should be configured: * Lock messaging connection details * Jans Auth messaginbg configuration
It's possible to modify them with jans-config-api.
First configuration Jans stores in ou=configuration,o=jans entry. This is reusable configuration. Other application which uses jans-core-message.jar library also should use it.
Default configuration after CE install when messaging API is not enabled:
jansMessageConf:
{
"messageProviderType": "DISABLED",
"postgresConfiguration": {
"connectionUri": "jdbc:postgresql://localhost:5432/postgres",
"dbSchemaName": "public",
"authUserName": "postgres",
"authUserPassword": "",
"messageWaitMillis": 100,
"messageSleepThreadTime": 200
},
"redisConfiguration": {
"servers": "localhost:6379"
}
}
It has 2 section for PostgreSQL (postgresConfiguration) and Redis (redisConfiguration) connection details.
messageProviderType can have 3 values: DISABLED, REDIS, POSTGRES
Full list of properties defined in jans-config-api-swagger.yaml.
Second configuration is needed for Jans Auth. In current version Jans Auth calls message API after access_token persistence/removal from/to DB from GarntService. Jans Messages API library provides generic API to hide actual PubSub messages publishing/receiving implementation.
This is default configuration after server install:
"lockMessageConfig": {
"enableTokenMessages" : false,
"tokenMessagesChannel": "jans_token"
}
tokenMessagesChannel specify channel name to send token messages.
The format of messages which Jans Auth issue is JSON. And it has minimum data for quick processing. Here is message pattern:
{"tknTyp" : "access_token", "tknId" : "token_identifier", "tknOp" : "add/del"}
Note: For demo purposes in Jans CE with PostgreSQL and Lock server selected to install messages enabled by default.
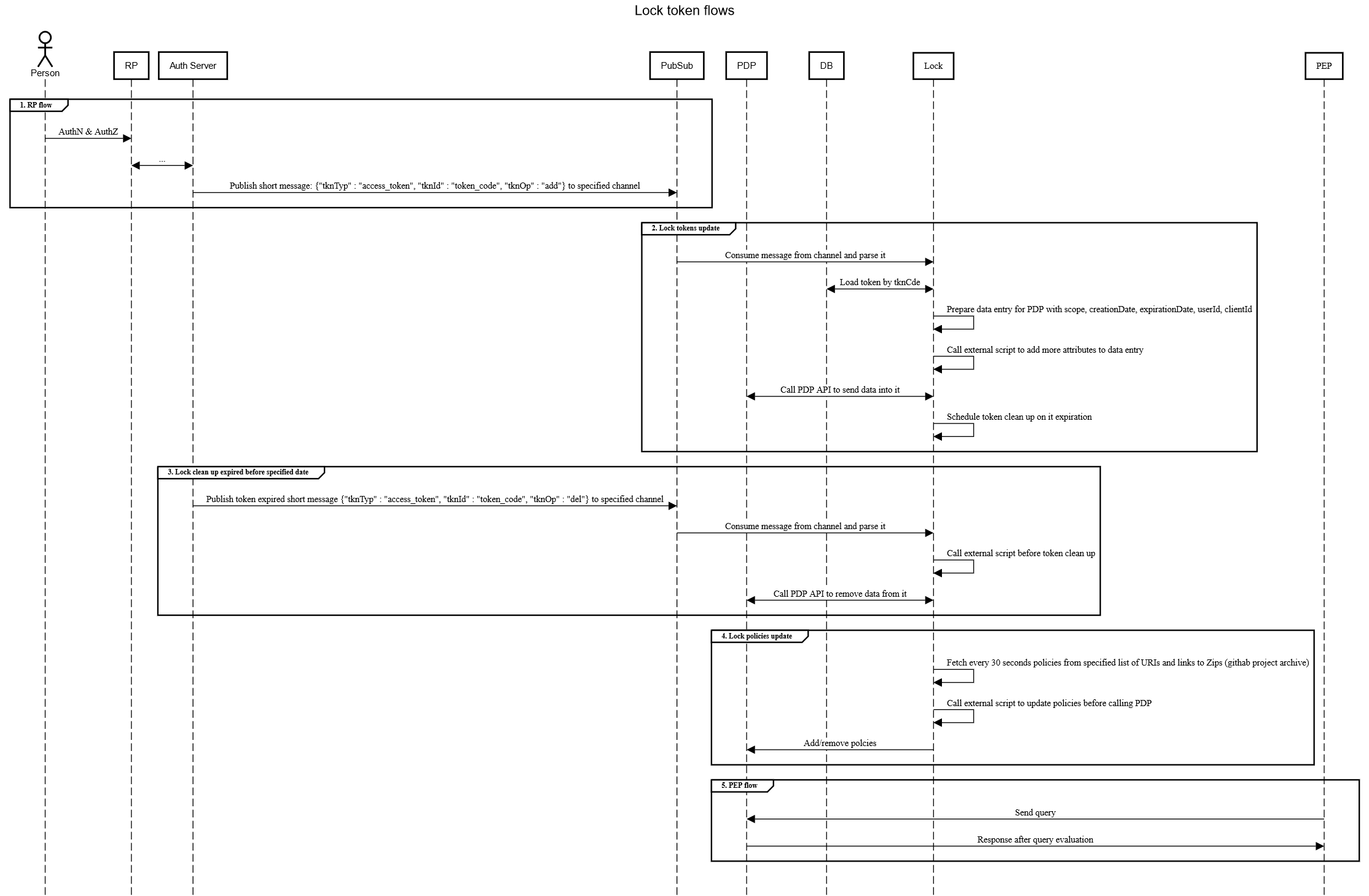
List of Lock flows:
Code:
title Lock token flows
actor Person
participant RP
participant Auth Server
participant PubSub
participant PDP
participant DB
fontfamily mono
group 1. RP flow
Person->RP: AuthN & AuthZ
RP<->Auth Server: ...
Auth Server->PubSub: Publish short message: {"tknTyp" : "access_token", "tknId" : "token_code", "tknOp" : "add"} to specified channel
end
group 2. Lock tokens update
PubSub->Lock: Consume message from channel and parse it
Lock<->DB: Load token by tknCde
Lock<->Lock: Prepare data entry for PDP with scope, creationDate, expirationDate, userId, clientId
Lock<->Lock: Call external script to add more attributes to data entry
Lock<->PDP: Call PDP API to send data into it
Lock<->Lock: Schedule token clean up on it expiration
end
group 3. Lock clean up expired before specified date
Auth Server->PubSub: Publish token expired short message {"tknTyp" : "access_token", "tknId" : "token_code", "tknOp" : "del"} to specified channel
PubSub->Lock: Consume message from channel and parse it
Lock<->Lock: Call external script before token clean up
Lock<->PDP: Call PDP API to remove data from it
end
group 4. Lock policies update
Lock<->Lock: Fetch every 30 seconds policies from specified list of URIs and links to Zips (githab project archive)
Lock<->Lock: Call external script to update policies before calling PDP
Lock->PDP: Add/remove polcies
end
group 5. PEP flow
PEP->PDP: Send query
PDP->PEP: Response after query evaluation
end
Created: 2023-11-06