Client Management#
Background#
A "client" is a piece of software either acting autonomously or on behalf of
a person. The OAuth framework defines the term client
here. OpenId Connect
clarifies
that:
OAuth 2.0 Clients using OpenID Connect are also referred to as Relying Parties (RPs)
Don't confuse a Client with either the Person or the Browser!
Client Security#
OpenID allows you to use as much security as you need. To a large extent, the
security of your implementation depends on what client features you select.
For example, let's just consider how the client authenticates itself to Jans Auth
Server, which is defined by the token_endpoint_auth_method in OpenID Connect
Client Metadata.
Obviously, using asynchronous secrets for authentication is more secure. The client configuration also determines what crypto is used for signing and encryption of tokens, what scopes are available to the client (which determines the extent of access to APIs), what grants are available, what is a valid redirect_uri, timeouts, whether to use a value or reference token, whether to expire the client, and several other options that impact security.
Client Management Tools#
A client can be created (and managed) by using one of the following tools offered by the Jans Auth server:
- Jans Config API
- Command Line Tool (CLI)
- Jans Text UI (TUI)
- OpenID Connect Dynamic Client Registration
The choice of tool should be made based on your business requirement.
- For ad hoc creation, the TUI is great.
- If you need to quickly script client creation (e.g. in a bash script) use the CLI
- Use curl to call the Jans Config API.
- To allow apps to register as OIDC clients, without a manual process, the OpenID
Connect Dynamic Client Registration (DCR) can be used.
A. OpenID Dynamic Client Registration#
Jans Auth server publishes the registration_endpoint in the OpenID
configuration JSON response, which you can find at .well-known/openid-configuration
in your specific deployment. Typically, it is
https://{hostname}/jans-auth/restv1/register
The OpenApi specification for /registration documents Jans Auth Server's specific implementation, which aligns with the requirements of OpenID Connect dynamic client registration. Also, check the Registration Endpoint documentation for more details on the steps involved in dynamic client registration.
B. Jans-CLI#
Below is a one liner to add a client.
./config-cli-tui.pyz --host $FQDN --client-id $MY_CLIENT_ID \
--client-secret $MY_CLIENT_SECRET --no-tui \
--operation-id=post-oauth-openid-client --data=my_client.json
For more information about how to use the Jans-CLI, see the docs
C. TUI#
To start registering a new client, navigate to
Auth Server->Clients->Add Client. This brings up a screen as shown below
with various sections to input client details.
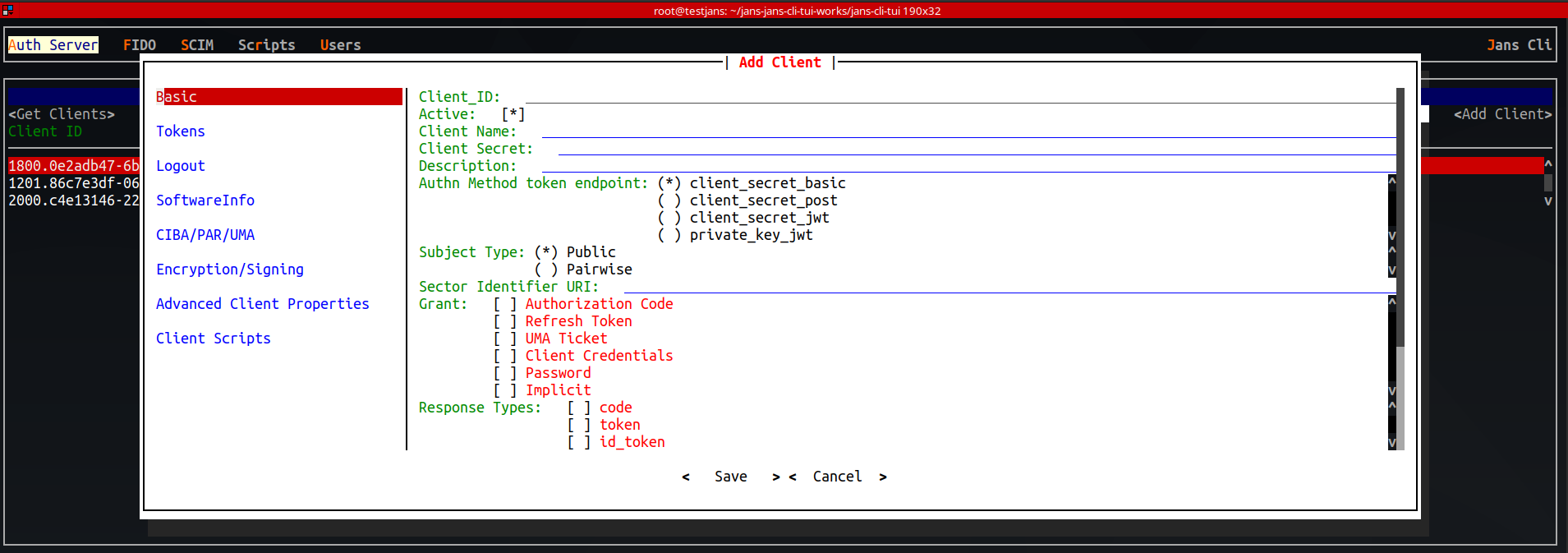
Refer to complete documentation here
D. Using curl commands#
To add a client via curl, see the information on the
curl documentation page.
Created: 2022-09-02